Ransomware as a Service (RaaS): What Businesses Need to Know
Cybercriminals use security gaps to infect computers with ransomware, destroy data and demand money. Ransomware as a Service (RaaS) is a new branch of ransomware evolution that makes ransomware more agile, allowing it to spread easily and infect more computers. This post explains what RaaS is, how it works and how organizations can protect their environment against this modern type of ransomware.
What Is Ransomware as a Service (RaaS)?
Ransomware as a Service (RaaS) is a cybercrime business model in which ransomware developers lease their malware to other cybercriminals (called affiliates) in exchange for a share of the profits from successful attacks or other payments. The approach of Ransomware as a Service is similar to that of Software as a Service (SaaS) in legal businesses. While SaaS can be beneficial, RaaS is illegal, dangerous and devastating.
RaaS operates through subscriptions, licensing fees or affiliate programs. Users (affiliates) get access to ready-to-use ransomware kits, dashboards and technical support. Some RaaS providers even have 24/7 support. The affiliates conduct the attack and collect a profit from extortion without the need to develop their own malware. Ransomware developers increase their profit because they don’t need to attack networks by themselves and spend time on it. These factors make the RaaS model mutually beneficial for cybercriminals.
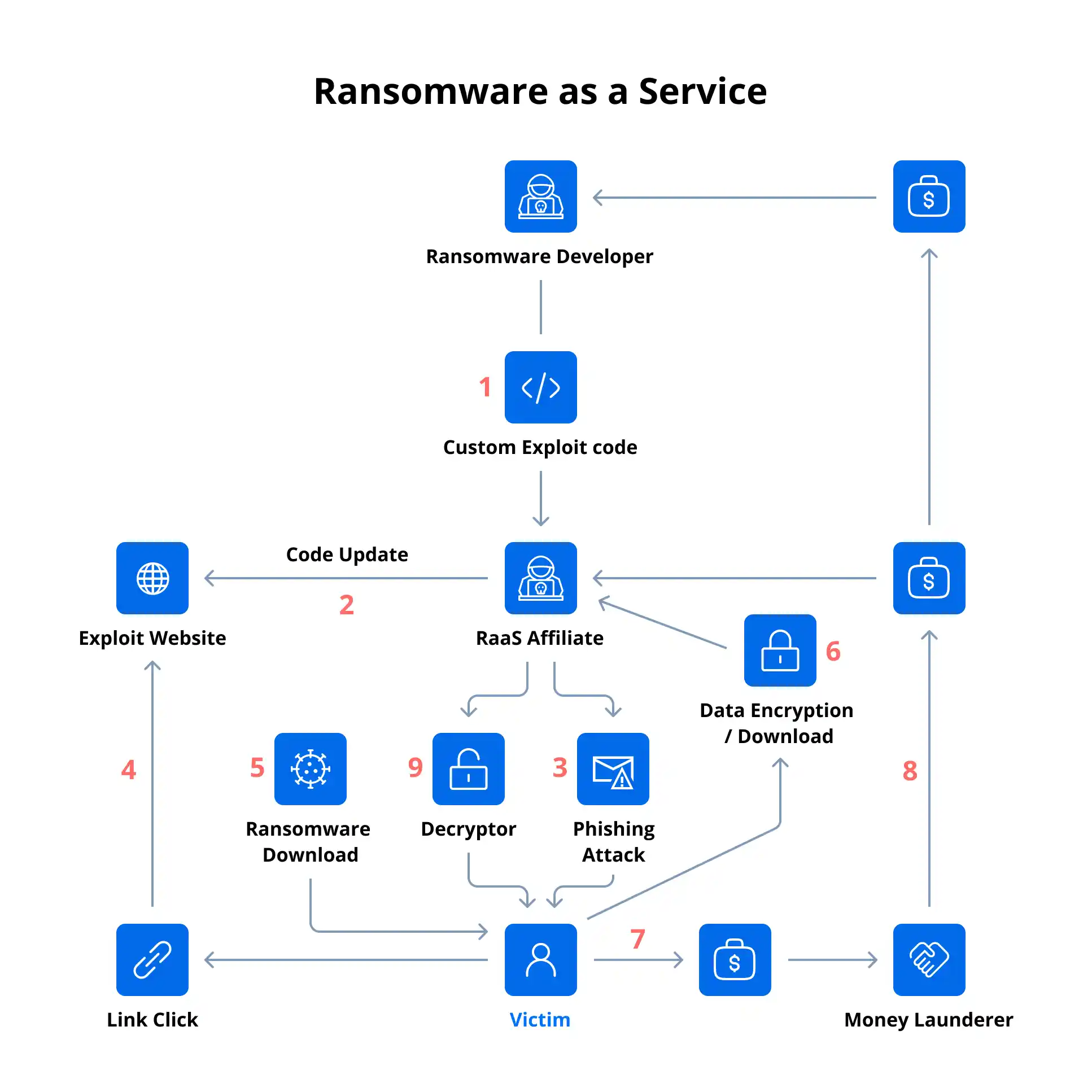
How Does Ransomware as a Service Work?
Ransomware as a Service (RaaS) operates like a commercial SaaS business but is used for criminal purposes. Cybercriminals implemented a division of labor to increase their efficiency: Ransomware developers write malicious code and affiliates develop more sophisticated attack methods and launch ransomware attacks. Let’s explain how Ransomware as a Service works.
Creation of the RaaS platform
- Developers build the ransomware code.
- They create a platform (often on the dark web) that they offer to affiliates. The platform may include:
- A control panel or dashboard;
- Customization options (ransom amount, target types, encryption settings);
- Support documentation and updates.
Affiliate recruitment
- RaaS operators recruit affiliates and other cybercriminals who want to use the ransomware.
- Affiliates sign up on the RaaS portal and may pay:
- A monthly subscription fee.
- A one-time fee. Affiliates pay once and share a percentage of ransom payments with the operators.
- Profit sharing by entering into a revenue-sharing agreement (for example, 70% to the affiliate, 30% to the developer).
Ransomware creators develop advertisement campaigns for their RaaS platforms and conduct marketing campaigns on the dark web, including underground forums. They actively try to recruit new affiliates and launch more ransomware attacks.
Attack execution by affiliates
- Affiliates launch attacks using the ransomware toolkit.
- Common methods of delivery:
- Phishing emails with malicious attachments or links;
- Exploiting software vulnerabilities;
- Compromised websites or Remote Desktop Protocol (RDP) brute-force attacks.
- Once executed, the ransomware encrypts the victim’s files and displays a ransom note demanding payment (usually in cryptocurrencies like Bitcoin).
Ransom payment
- Victims are directed to a payment portal (often accessible via the TOR network) where they can pay the ransom. Payments are usually made in cryptocurrencies because they are difficult to trace.
- Some RaaS operations offer a help desk for victims to get payment instructions or “proof of decryption”.
Revenue sharing
- Once a ransom is paid:
- The affiliate and the RaaS provider automatically split the money based on their agreement.
- The affiliate may receive tools to decrypt the files and send them to the victim.
Continuous evolution
- The RaaS developers continue updating the ransomware to avoid detection by antivirus software.
- They may also upgrade features, support new cryptocurrencies or offer new exploits.
|
Stage |
Description |
|
Development |
The ransomware is created by skilled programmers |
|
Recruitment |
Affiliates sign up to use the service |
|
Deployment |
Affiliates launch attacks using the RaaS toolkit |
|
Payment |
Victims pay the ransom through encrypted portals |
|
Profit Sharing |
Earnings are split between developers and affiliates |
RaaS has industrialized cybercrime by making ransomware a plug-and-play service. It allows anyone without technical skills to profit from cyberattacks, significantly increasing the threat landscape.
Notable RaaS Groups and Variants
Some well-known ransomware creators are also top Ransomware as a Service providers. The RaaS model allows gangs and organized groups of criminals to conduct destructive attacks.
REvil (Sodinokibi)
REvil is known for the largest registered ransom demand in history. This Ransomware as a Service was mainly active between 2019 and 2021. REvil uses the double extortion tactics: Encrypt files and threaten to leak data. It even offered a user-friendly portal for affiliates.
Notable attacks:
- JBS (the world’s largest meat supplier)
- Kaseya VSA software supply chain attack
Origin: Believed to be Russia.
Status: Disrupted by international law enforcement.
DarkSide
DarkSide was active in 2020 and 2021. This RaaS claimed to avoid targets in healthcare and education. DarkSide operated like a corporate business, with PR and support. The most notable attack was against Colonial Pipeline, which caused fuel shortages in the USA. Salsa20 and RSA encryption were used.
Origin: Russia-linked group.
Status: Shut down after the Colonial Pipeline backlash, but remnants rebranded (e.g., BlackMatter).
LockBit
LockBit was released in 2019 and is still active today. Notable attacks are Accenture, Royal Mail UK and some government agencies. LockBit 3.0 added bug bounty programs and data leak sites. The Ransomware as a Service provides automation and customizable affiliate tools. In 2022, Lockbit was the most popular ransomware in the world.
Origin: Possibly Eastern European.
Status: Still active, despite takedowns (as of 2025).
Conti
Conti ransomware was active between 2020 and 2022 and the Irish Health Service Executive (HSE) was one of its notable targets. Cybercriminals used the double extortion tactics and their own infrastructure (not TOR-based). Conti leaks exposed internal chat logs in 2022.
Origin: Russia-linked, possibly a successor to Ryuk.
Status: Disbanded, many members likely joined other groups.
BlackCat (ALPHV)
BlackCat has been working since 2021 and has been used to conduct successful attacks against universities, healthcare institutions and critical infrastructure. It was written in Rust, which makes it more challenging to detect. This ransomware uses triple extortion: encryption, data theft and DDoS threats.
Origin: Suspected former affiliates of DarkSide or REvil.
Status: Active and evolving.
Hive
Hive ransomware was active from 2021 to 2023 and was used to attack the healthcare sector, including hospitals. It is known for fast encryption and data theft. This ransomware used Remote Desktop Protocol, remote connection protocols and VPN to gain initial access to the victim’s network. The FBI seized the infrastructure of this Ransomware as a Service in January 2023.
Ransomware groups often rebrand, merge or re-emerge under new names. The RaaS ecosystem is resilient and keeps evolving, with newer groups frequently building on the tactics of their predecessors.
Why RaaS Is a Growing Cybersecurity Threat
Ransomware as a Service increases the frequency, scalability and damage of cyberattacks by making ransomware accessible. The traditional approach requires high skills and more time to execute an attack. The platforms often come with step-by-step guides, technical support and user-friendly dashboards.
Multiple affiliates can use the same ransomware variant to target hundreds or thousands of victims simultaneously. This “franchise model” massively scales up the volume and geographic reach of the attacks. A large number of RaaS groups run like legitimate SaaS companies, offering:
- Service tiers (basic vs premium)
- Affiliate vetting processes
- Victim negotiation services
- Help desks for victims to pay ransoms
This professionalization makes the services more reliable and appealing to would-be attackers. RaaS groups operate on the dark web using anonymized communication and payment tools. Affiliates may be spread across different countries, complicating the job for law enforcement agencies.
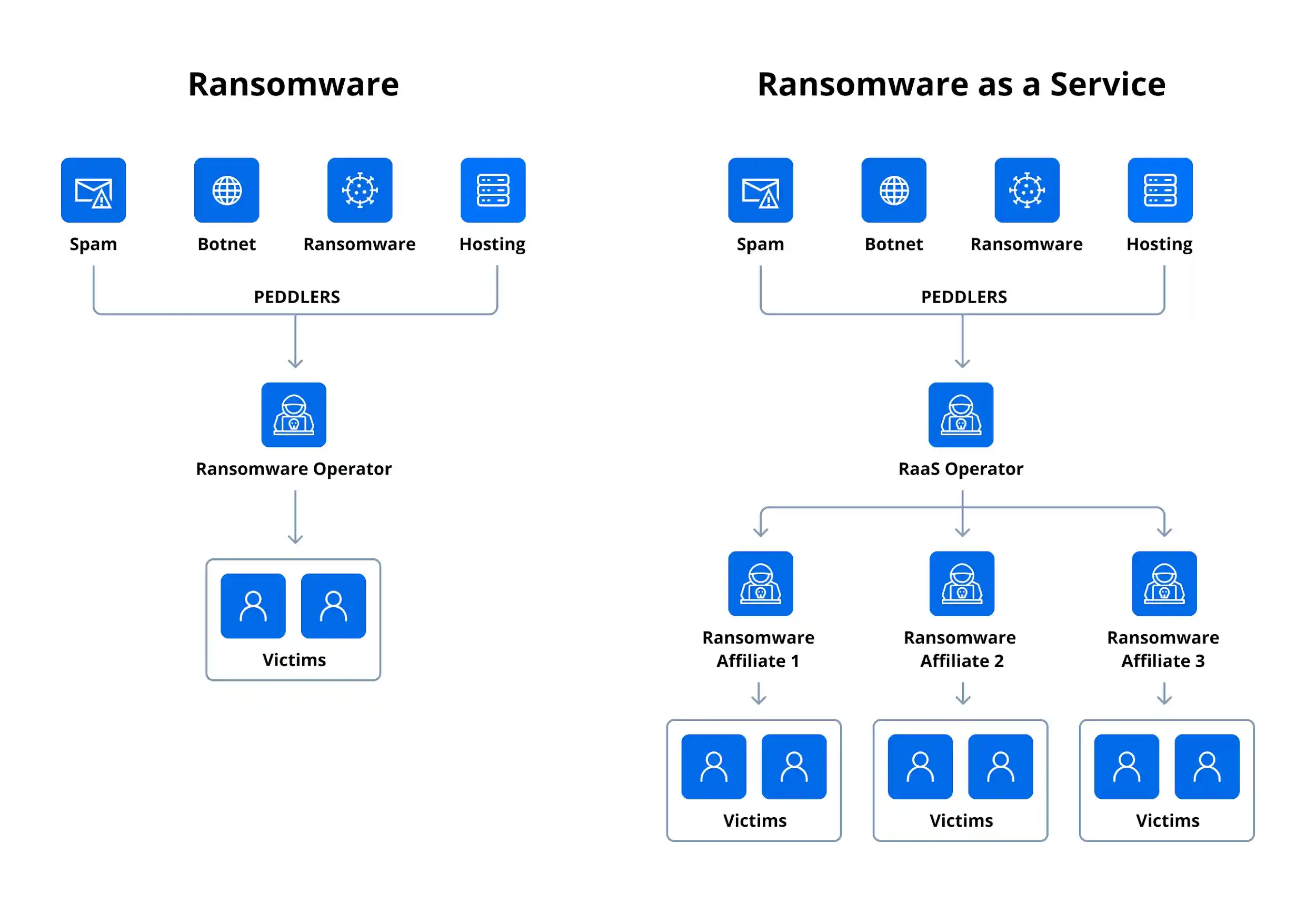
Affiliates and developers split large ransom payments, sometimes millions of dollars per attack. Cryptocurrencies make it easier to demand and launder ransom payments anonymously. RaaS enables attackers to hit a wide range of targets. Sectors that often lack the resources to fully defend against such threats and are more likely to pay are among the favorite targets.
If a RaaS developer is caught, affiliates can find another provider to resume their operations. Conversely, ransomware developers can hire another one if an affiliate is caught and jailed. This factor makes Ransomware as a Service more resilient.
RaaS developers frequently update their malware to evade detection. They incorporate:
- Zero-day vulnerabilities
- Obfuscation techniques
- Advanced encryption
- Some RaaS creators even offer bug bounty programs for other cybercriminals to improve their tools.
|
Factor |
Why It Matters |
|
Low skill requirement |
Increases the number of attackers |
|
Scalable model |
Mass attacks become easy to launch |
|
Big financial rewards |
More motivation for cybercriminals |
|
Professional operations |
Higher success rates for affiliates |
|
Rapid evolution |
Harder for defenders to keep up |
|
Broad target base |
Hits essential, underprotected sectors |
|
Hard to trace |
Limits law enforcement effectiveness |
RaaS is democratizing cybercrime, turning ransomware into a commodity. Its widespread availability is creating a global epidemic of attacks, making it one of the fastest-growing threats in cybersecurity today.
Business Risks and Pitfalls of RaaS Attacks
Ransomware as a Service poses serious business risks that are much more dangerous than temporary service disruptions. A successful ransomware attack can terminate operations, damage an organization’s reputation and lead to long-term financial and legal consequences.
Operational disruption occurs when systems, applications and files become inaccessible after a ransomware attack that encrypts/destroys files. As a result, business operations may halt for hours, days or weeks.
Financial loss includes direct and indirect damage. These costs may include:
- Ransom payments, often made in cryptocurrency without any guarantee of recovery.
- Recovery costs. If you lose unique data, it is difficult to recreate it. Previously, it was possible to restore some data after ransomware attacks by knowing some tricks posted by cybersecurity experts. However, nowadays, such recovery scenarios are rare.
- Downtime and lost productivity. Customers may avoid buying your products and services after learning about a service disruption caused by a ransomware attack.
- Cybersecurity incident response. An organization may need additional software and hardware to restore normal operations after a ransomware attack.
- Extra costs: Hiring third-party experts, legal counsel or negotiators requires additional payments.
Non-compliance with data protection regulations (e.g., GDPR, HIPAA, CCPA) can result in legal and regulatory consequences. Potential issues can include mandatory breach notifications, lawsuits from customers or partners, fines and legal penalties. The most dangerous ransomware uses double or triple extortion tactics when data is stolen before encryption.
Organizations that pay the ransom can become a recurring target, especially if they don’t fix existing vulnerabilities. Even after systems are restored, hidden malware or backdoors may remain. This can impact the company’s reputation and cause loss of trust from customers and investors. Some cyber insurance policies do not cover ransomware or have strict conditions.
How to Protect Your Organization from RaaS
The measures to protect against Ransomware as a Service are identical to usual ransomware protection measures. Organizations must use a multi-layered strategy that combines technology, processes and people. You should place enough obstacles between the hackers (affiliates) and the organization’s network assets.
- Protect all computers within your organization by installing reliable and modern antivirus software (including the computers of remote workers).
- Configure firewalls to protect your network. Close unused ports and configure firewall rules. Use network segmentation to limit the spread of ransomware in case of infection.
- Educate users to notice the first signs of ransomware attacks. Users must learn how ransomware can spread and the main attack vectors, such as phishing emails, malicious links and social engineering tricks. Most RaaS attacks start with phishing or human error.
- Configure malware protection for emails using spam filters and cybersecurity tools.
- Configure role-based access control. Use strong passwords that are difficult to hack. Use multi-factor authentication for the most critical services, such as email. The principle of least privilege and zero-trust architecture can be effective measures against ransomware services. RaaS affiliates often exploit weak or reused credentials.
- Install security patches to patch software vulnerabilities in operating systems, applications and firmware. This can reduce the network attack surface. RaaS kits often use known exploits to breach vulnerable systems.
- Monitor the IT infrastructure. Configure monitoring software to monitor network, CPU and storage load to detect abnormal activity that can be a sign of a ransomware attack (file encryption significantly loads a processor and disk). Monitor unusual login patterns and incorrect login attempts to detect unauthorized access. Early detection can stop ransomware before encryption begins.
- Back up data regularly. Perform backup testing to ensure that you can recover data in case of a disaster. Backups are the last line of defense if encryption occurs.
- Create an incident response plan, disaster recovery plan and business continuity plan. Being prepared can dramatically reduce downtime and damage.
The Role of Backup in Ransomware Resilience
Backups are critical to protect data against ransomware, including attacks made with Ransomware as a Service. A reliable backup strategy allows organizations to avoid paying the ransom and recover data quickly.
When you have a backup, you can:
- Restore encrypted or deleted data without the decryption key. This minimizes the financial and ethical risk of paying cybercriminals.
- Use a reliable backup system to quickly resume business operations and minimize downtime. Depending on recovery capabilities, downtime can be reduced from days or weeks to hours.
- Benefit from cost-effective recovery.
Investing in a robust backup system is far less expensive than paying a ransom, dealing with downtime or regulatory penalties.
Follow the recommended practices for ransomware protection using backups:
- Follow the 3-2-1 backup rule. Keep three copies of your data on two media types, with one copy off-site or offline.
- Configure a regular backup schedule to ensure minimal data loss.
- Use immutable backups to prevent ransomware from encrypting or deleting backups.
- Use offline or air-gapped backups to keep a copy completely disconnected from the network.
- Run automated backups. This practice reduces human error and ensures consistency.
- Enable backup encryption to protect data at rest and in transit.
- Test backups and recovery procedures to ensure backups work and can be restored quickly.
- Use segregated access control and limit access to backup systems to reduce insider threats.
There are some practices you should avoid:
- Relying only on cloud backups (they can be targeted too);
- Failing to test recoveries regularly;
- Keeping backup systems on the same network as production systems;
- Not detecting ransomware that has already infected backup data.
Businesses with secure, tested and isolated backups can recover fully without paying the ransom. Those without backups often face crippling losses, weeks of downtime or permanent data loss. Backups aren’t just a precaution but a core part of any ransomware resilience strategy. However, they only work if they are frequent, secure, tested and isolated.
The Future of Ransomware as a Service (RaaS)
RaaS will likely bring more advanced, widespread and persistent threats as cybercriminals continue developing their tactics and infrastructure. In the coming years, we can expect the following features:
- More sophisticated malware. Ransomware powered with artificial intelligence (AI-powered ransomware) could automate target selection, encryption patterns and evasive tactics. Advanced RaaS tools may integrate machine learning to bypass security defenses more intelligently.
- Increased professionalization of cybercrime. RaaS operations will become even more corporate-like, offering tiered pricing plans, service level agreements and customer service portals. The trend is that RaaS groups will function like black-market SaaS providers. Pressure tactics will become more personal and aggressive.
- Targeting of critical Infrastructure and operational technology systems. RaaS groups will target industrial control systems in energy, transportation and healthcare sectors, especially outdated and less secure systems. The focus is shifting towards high-impact sectors with urgent uptime needs.
- Greater use of initial access brokers. Specialized criminals can sell access to already-compromised systems. As a result, RaaS affiliates can skip initial infiltration and move straight to deployment.
- Stronger data protection measures. Organizations must implement more reliable data protection measures and cybersecurity systems, including software using AI-based mechanisms for early ransomware detection. The emphasis will be on resilience and recovery, not just prevention. Defensive strategies will evolve in response to advanced threats. Cyber insurance policies may discourage or restrict ransom payments.
Conclusion
Ransomware as a Service (RaaS) is the modern stage of ransomware development with a distributed and more effective organization than legacy ransomware. RaaS allows cybercriminals to launch more attacks, meaning organizations must better protect their infrastructures. Data backup is one of the most important data protection measures, in addition to preventive cybersecurity measures. Invest in reliable data protection solutions such as NAKIVO Backup & Replication, perform regular backups, follow the best practices and avoid paying a ransom in case of an attack.